17 Apr Smartphone wallets revolutionise physical identity and access management
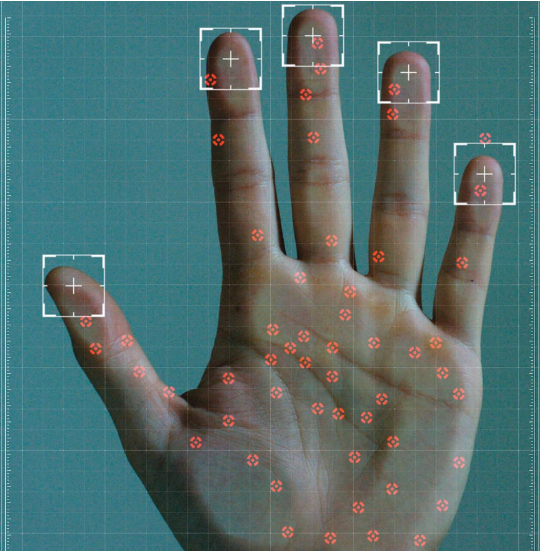
In today’s digital landscape, smartphones have evolved into essential multifunctional tools, serving as central hubs for everyday tasks such as payment, identification, health monitoring and communication. Patrick Wimmer, John Harvey and Carl Fenger, of LEGIC Identsystems, explain more about smartphone wallets and their use for...